The INSPIRE-5Gplus project
Ramon Sanchez-Iborra
University Center of Defense, Spanish Air Force Academy
Antonio Skarmeta
University of Murcia, Spain
Jordi Ortiz
University of Murcia, Spain
The recently arrived 5G architectures will enable a plethora of services and applications never imagined some time ago. However, its complex network infrastructure is prone to suffer cybersecurity attacks that must be tackled in order to ensure users’ privacy and security. In this line, the Horizon-2020-funded INSPIRE-5Gplus project aims at progressing the security vision of 5G & beyond systems by designing and developing a smart, trustworthy and liability-aware security platform for these kinds of systems. To this end, state-of-the-art technologies such as Zero-Touch Network & Service Management (ZSM), Software Defined Security (SD-SEC) modes, Artificial Intelligence (AI)-based techniques, and Trusted Execution Environments (TEE) are being adopted to provide a security aware architecture and its associated closed-loop of security functions.
To this end, a High-Level Architecture (HLA) for supporting zero-touch end-to-end smart network and service security management in 5G and beyond networks has been designed and is being implemented. By leveraging the flexibility of softwarization technologies (e.g., Software Defined Networks (SDN)/Network Function Virtualization (NFV)) and AI/ML techniques, the INSPIRE-5Gplus HLA will permit end-to-end orchestration and management that enforce and control security policies in real-time and adapt to dynamic changes in threats landscape and security requirements in 5G and beyond networks. Autonomous network orchestration is managed by a closed-loop mechanism that relies on continuous monitoring information to achieve the desired zero-touch automation driven by the introduction of AI techniques. Besides, the project is defining advanced mechanisms to foster trustworthiness of smart SD-SEC solutions in a multi-tenant/multi-domain setting as well as new schemes to enforce liability of involved parties when security breaches occur and/or system fails.
In the following sections, this article explores the overall INSPIRE-5Gplus’ HLA and the security management closed-loop on which the project relies, to provide not only protection but also trustworthiness and liability in a fully automated end-to-end smart network and management framework.
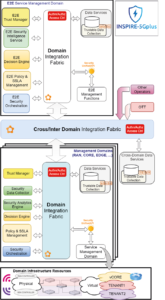
Figure 1: INSPIRE-5Gplus’ High Level Architecture (HLA)
INSPIRE-5Gplus architecture
The 5G architecture deals with a huge diversity of services, applications, and use cases that can be classified into three different families: enhanced Mobile Broadband (eMBB), Ultra Reliable Low Latency Communications (URLLC) and massive Machine Type Communications (mMTC). This is achieved by providing a unified and interoperable ecosystem of different and complementary technologies. The promised omnipresence of 5G and beyond networks calls for a secure and trustworthy system to meet the stringent requirements of the aforementioned families of use cases and services.
In order to deal with this variety of applications INSPIRE-5Gplus has defined an end-to-end HLA supporting the separation of security management concerns. This framework will exploit novel AI-driven security models to enable smart and proactive security management that can intelligently predict, prevent, detect and mitigate cyber threats. On the other hand, novel SDN/NFV orchestration and management mechanisms will be integrated to enforce and control security policies in real-time and adapt to dynamic changes in threats landscape and security requirements.
Figure 1 presents the high-level architecture, which is split into security management domains (SMDs) to support the separation of security management concerns. Each SMD is responsible for the intelligent security automation of resources and services within its scope. The E2E SMD is a special SMD that manages security of E2E services (e.g. E2E network slice) that span multiple domains. The E2E SMD coordinates between domains using security orchestration. The decoupling of the E2E security management domain from the other domains allows escaping from monolithic systems, reducing the overall system’s complexity, and enabling the independent evolution of security management at both domain and cross-domain levels.
Each of the SMDs, including the E2E SMD, comprises a set of functional modules (e.g. security intelligence engine, security orchestrator, trust manager) that operate in an intelligent closed-loop way to enable software-defined security (SD-SEC) orchestration and management. This functionality will be further explained in the next section. Each functional module provides a set of security management services that can be exposed inside the same domain or cross-domain to the authorized consumers, using the domain-integration fabric or the cross-domain integration fabric, respectively.
In addition to a multi-domain design, the INSPIRE-5Gplus security architecture is extensible to multi-operator and Over-The-Top (OTT) environments by considering their security threats and requirements. Although it is developed with a focus on single operator environment needs, the inter-domain fabric provides an inherent capability for security management among disparate networks as shown in Figure 1. The security-aware services available from the operator are made accessible to third parties, such as other operators or OTT services, via the inter-domain integration fabric exposed services. In the same way, this same operator may reach other operators’ inter-domain fabric to accomplish an E2E service request originated locally.
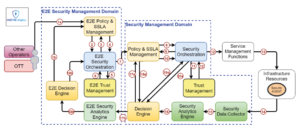
Figure 2: INSPIRE-5Gplus’ multi-domain closed-loop interactions
Security management closed-loop
INSPIRE-5Gplus has adopted a closed-loop-approach in which a series of automatic security functions are able to coordinate for inspecting the network infrastructure and its crossing traffic in order to detect security anomalies and take automatic measures to mitigate the impact of possible attacks. To this end, the entities forming the HLA integrate cognitive capabilities through the exploitation of novel AI/ML-based security techniques. Thus, the security functions are capable of interacting among each other in an autonomous way, following the ZSM paradigm.
There are two starting points for the whole process (see Figure 2) at the End-to-End (E2E) Security Management Domain (SMD) level (1a,1b), both implying the provision of an E2E Security Service Level Agreement (SSLA) coming from an external entity (e.g. OTT) or internally as an AI based reaction, such as those provided by the E2E Decision Engine.
Once the SSLA arrives to E2E SSLA Manager, a refinement process (2,3,4) is performed producing an orchestration High-Level Security Policy Language (HSPL) which in turn is refined in multiple orchestration Medium-Level Security Policy Language (MSPL), at least one per involved SMD. This HSPL to MSPL refinement profits from trustworthiness scores calculated via smart-contracts and taking advantage of the historical behavior of the system among others (5,6).
The solution selected (7) needs to be enforced on the different SMDs, which in turn are responsible of the infrastructure. The Orchestration MSPLs are refined onto Domain MSPLs while taking care of possible dependencies as well as conflicts between them (8,9,10). Similarly to the trustworthiness score-based solution prioritization done at E2E level, at this level not only the possible solutions are valuated (11) but also the infrastructure on which they are going to be deployed. As a result of this process the precise interactions with the infrastructure elements (12) are obtained and the system’s behavior is altered (13).
The behavior of the system is constantly monitored, in particular looking for security flaws, and events are reported to the Security Analytics Engine. When an anomaly is detected, Decision Engine at the SMD level is informed (16).
AI techniques are employed to generate a mitigation in MSPL form again inspected for conflicts with the already enforced policies (17a,18a). Finally (19a,20a) the SMD loop is closed by providing the Security Orchestrator with the new policy that is altering the system’s behavior again.
Alternatively, or by explicit decision, E2E Security Analytics Engine is informed (17b) of the anomaly and the countermeasure decided, if any. The E2E Security Analytics Engine will inform the E2E Decision Engine (18b) that again may decide to provide a countermeasure but probably affecting neighboring SMDs via the E2E Security Orchestration (19b) therefore closing the E2E loop.
Conclusion
The realization of secure and trustworthy 5G systems is crucial for a firm digital transformation. To this end, the INSPIRE-5Gplus project is focused on developing a state-of-the-art software-defined security orchestration and management framework for future connected systems (5G & beyond) and pervasive services. The designed architecture empowers zero-touch security services for protection, trustworthiness and liability in managing 5G & beyond systems across multiple domains leveraging emerging techniques, including ZSM, AI/ML, DLT and TEE. The foundations of this security architecture is based on enabling an intelligent closed-loop of security operations that takes into account the constitution of multi-domain architectures and the need of multi-level loop termination. INSPIRE-5Gplus establishes the basis for intelligent, secure and trustable 5G deployments by addressing the key security challenges through vertical applications applying the described closed-loop and HLA.
Further information
INSPIRE-5Gplus website – https://www.inspire-5gplus.eu


